Cloud Smart Journey
In this section of the playbook, you can learn more of how stakeholders can utilize our cloud services. Pick the one that’s closest to you or browse to see the guidance for various stakeholders.
Cloud Smart Journey
Consumer Persona - Business Application Team - Follow the Cloud Smart Journey of a business application team looking to modernize their applications
Producer Persona - GSA Security Team - Follow the Cloud Smart Journey of GSA Security in their process of updating or implementing a cybersecurity feature
View Cloud Smart Journey PersonasThe purpose of the Intake Phase is to begin a collaborative partnership with the tenant, obtain an understanding of the application needs through the Lean Intake Assessment and application Requirements Template, and assess cloud readiness.
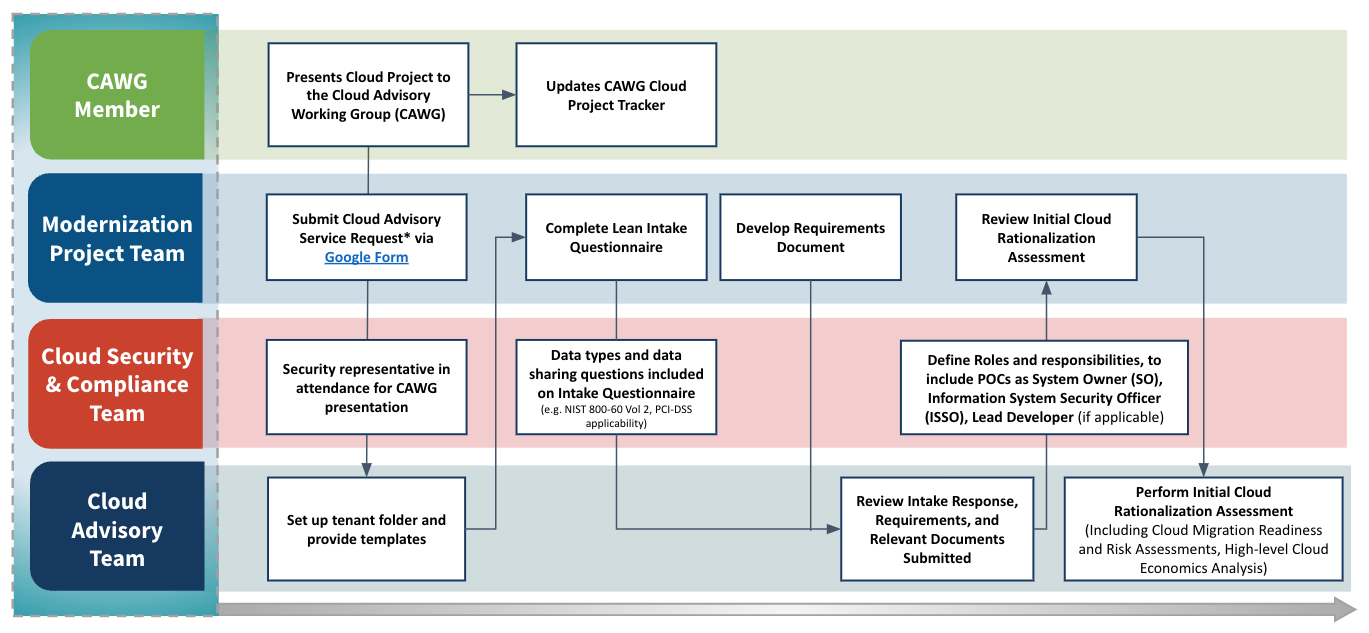
Cloud Advisory Services*: Any changes related to the architecture, operational model, security boundary to existing services or products. New Capability enablement or Capability enhancements to existing products. New product(s) to be brought into FCS to develop to be a new service.
Google Form: Click on this LINK and follow the navigation path below within GSA Service Now
Navigation Path: Home > Service Catalog > Enterprise Services > Cloud Services > CISS Cloud Service
- Completed intake request
- Increased understanding of tenant needs
- Completed set of requirements
- Completes Security section of the Intake Questionnaire
- Defines roles and responsibilities, to include POCs such as System Owner (SO), Lead Developer (if applicable)
The purpose of the Advisory Phase is to orient tenants to the Cloud Smart Journey process; and validate requirements which will drive the assessment and target model leading to a cloud migration rationalization strategy.
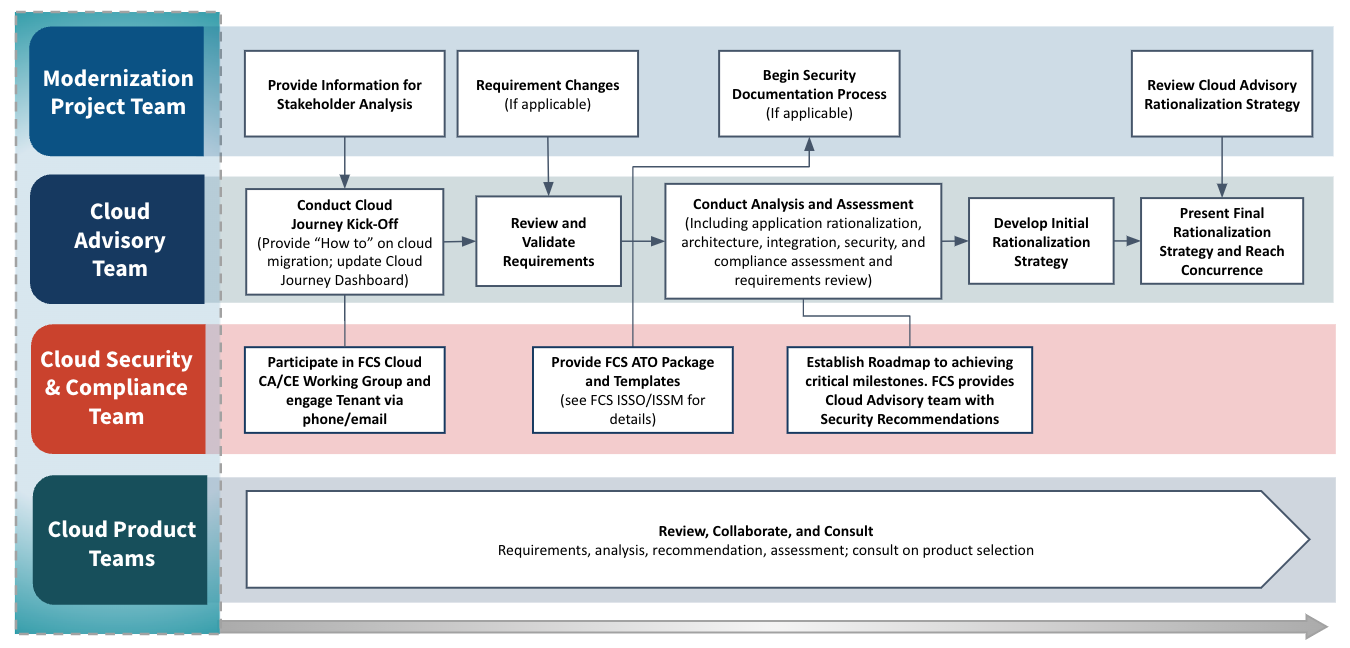
- Completed assessment
- Initial rationalization strategy
- Obtains FCS ATO Package and Templates
- Provides details for planned System/Data Interconnections; including disclosure of any additional baseline security requirements
- Discloses all necessary security requirements to Cloud Advocate
The purpose of the Enablement Phase is to collaborate with FCS Security and FCS Product Team to develop and gain concurrence on the Cloud Modernization Plan. Completion of the Cost Estimate, Schedule, and Onboarding Checklist are put in place to execute the Cloud Modernization Plan.
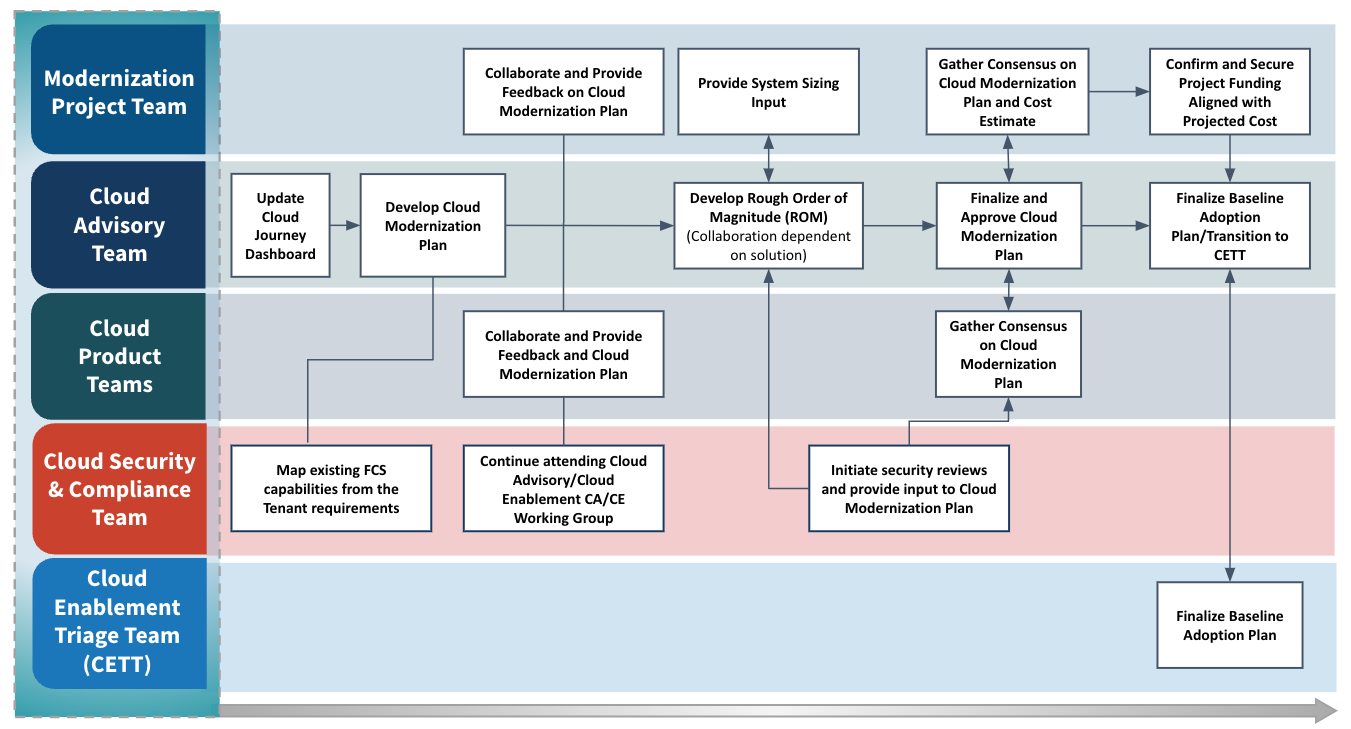
- Rough Order of Magnitude
- Cloud Modernization Plan
- Clear and achievable strategy to addressing FCS security requirements (example: initial control gap assessment)
- Plans to address security artifact delivery and identifying potential delivery risks
- Draft Rough Order of Magnitude (ROM) based on ISSO checklist and other considerable factors
- Detailed System Description (Use and Purpose required)
- Synchronize development timeline with security artifact(s) development
- Determination of applicable Security Documents (example: incident response plan may not be applicable)
The purpose of the Adoption Phase is to enable production readiness, complete all security requirements to achieve the ATO, implement supporting structures to drive adoption, and monitor the project from kickoff to launch to ensure the anticipated outcomes of the Cloud Modernization Plan are met.
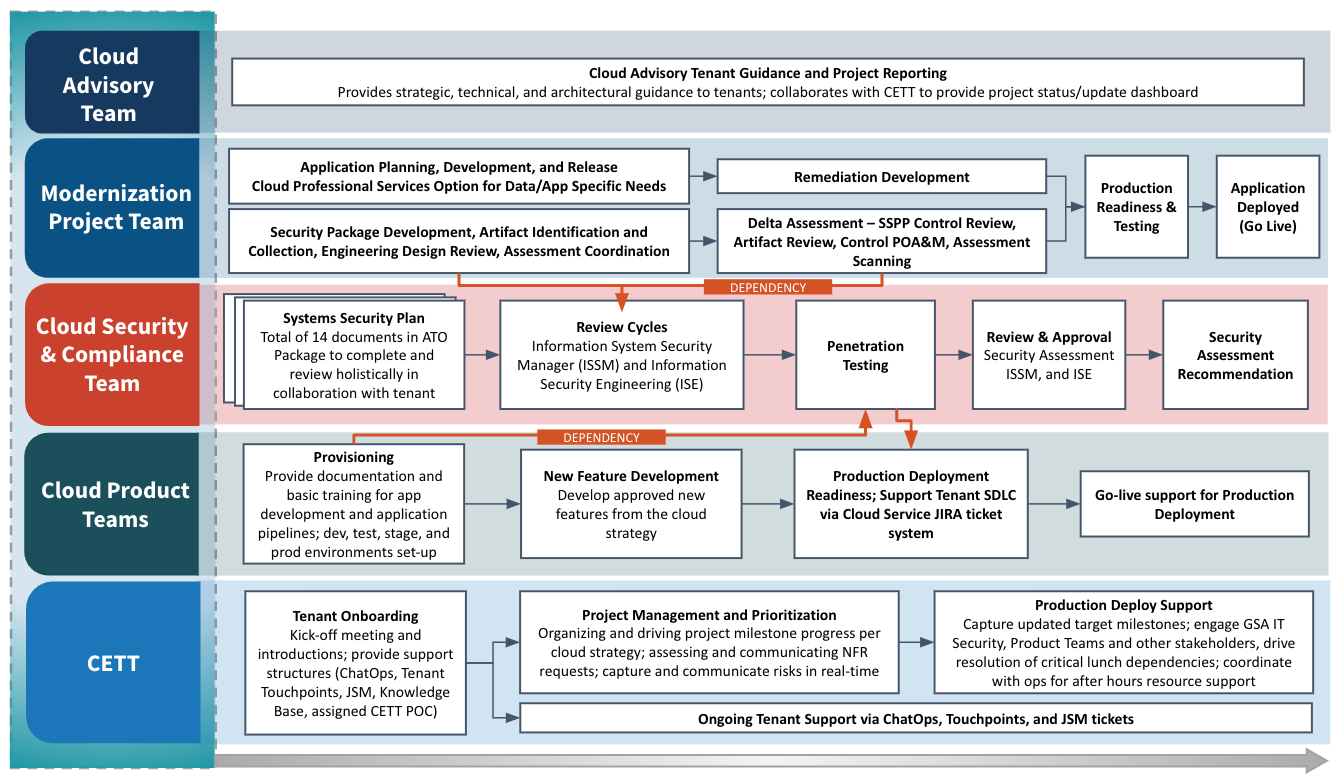
- Tenants are fully active and onboarded to their environment with operational support structures in place
This Kickoff is the first meeting with CETT on continuation of phases in the Cloud Smart Journey. This presentation will get things started with the right teams and help get everyone on the same page with clear communication between all parties involved. Click on this LINK to view the presentation.
- Clear understanding of Security Assessment Plan (SAP) amongst key stakeholders
- Initial Security Authorization timeline is approved by all-parties
- Final FIPS 199 categorization is determined
- PTA and PIA Forms are reviewed and approved (if applicable)
- Final e-Auth Level is determined
- Security review and approval of draft SSPP
- Actionable next steps to initiating and completing applicable Security Documentation such as but not limited to: Contingency Plan (CP), Business Impact Assessment (BIA), Incident Response Plan (IRP)
- Security Assessment Report (SAR) and Authorization decision are obtained
The purpose of the Optimization Phase is to provide ongoing service support and maintenance for onboarded tenants, track cloud utilization measures, and partner on continuous modernization efforts.
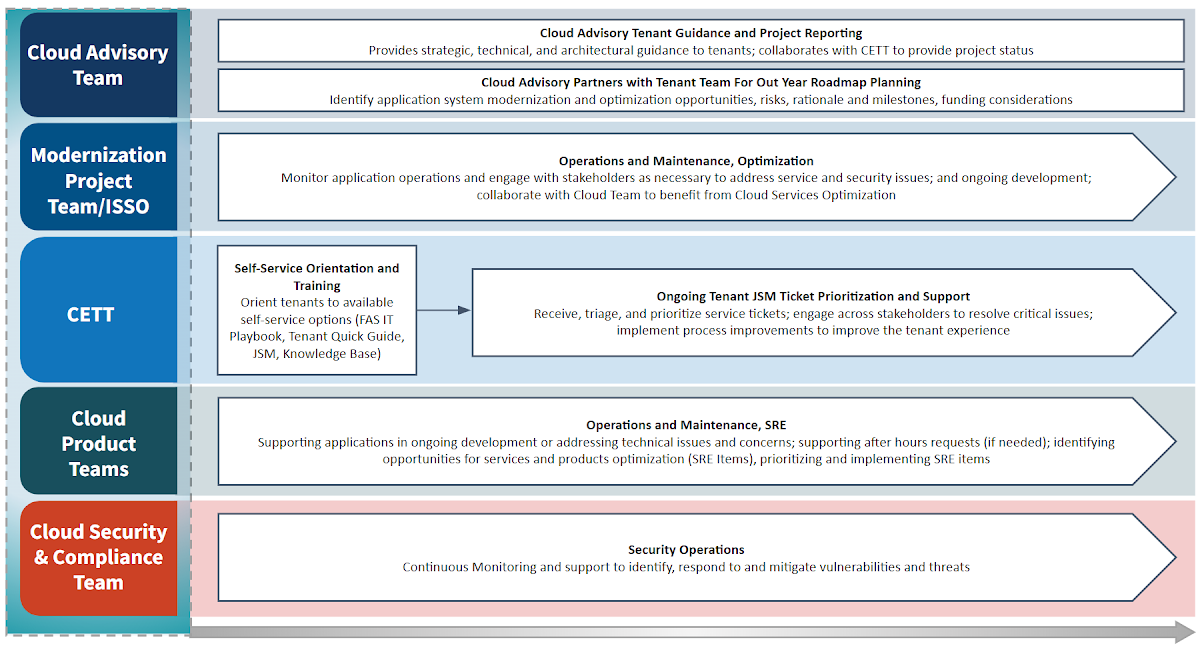
- Tenants are self-managed and operating in optimized environments
- Feedback is collected to achieve continuous improvement
- Discussion for ongoing audits
- Vulnerability Scans (Weekly/Ad-Hoc)
- Active ATO Progress (e.g. re-authorization)
- Planned Security Activities
- Security Roadblocks
- Executive Orders, Updates to NIST Publications/RMF/ FISMA Data Calls
- ISSO Self Assessments and Checklist status update
- Plan Of Action and Milestones (POA&M) updates
- Discuss Risk Based Decisions for risk acceptance (when applicable)
- Review list of SecOps approved security tools to determine tenant's operational needs.
- Payment Card Industry (PCI-DSS) Assessment progress (if applicable)

